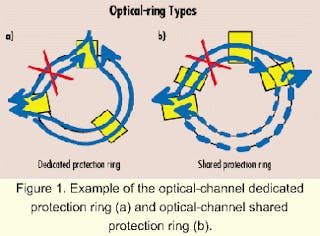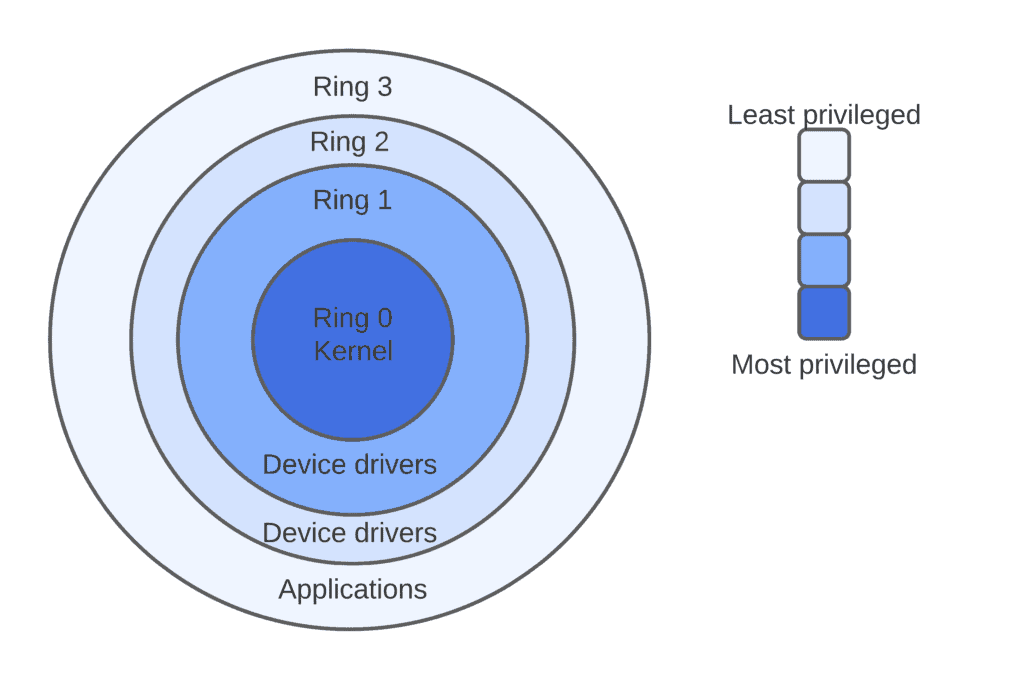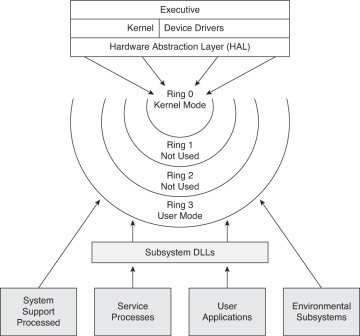
Security Architecture | CISSP Exam Cram: Security Architecture and Models | Pearson IT Certification

Figure 4 from Latch-up ring design guidelines to improve electrostatic discharge (ESD) protection scheme efficiency | Semantic Scholar

Evil Eye Diamond Ring / Protection Ring / Gift For Daughter / Eye Protection Ring / Gift For Her / Womens Stacking Ring / Stackable Bane
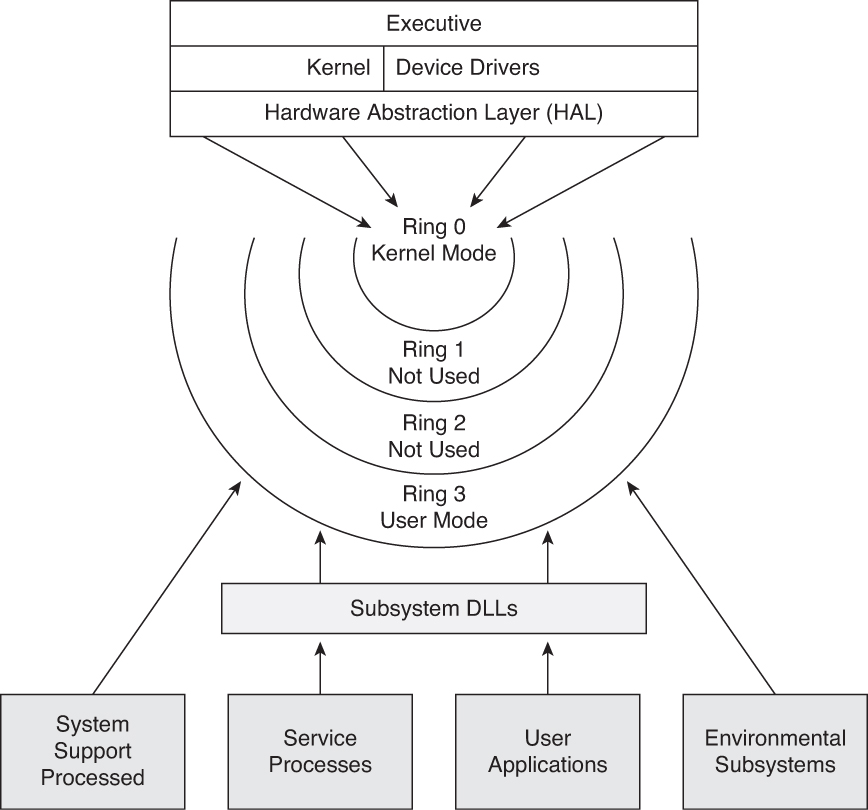
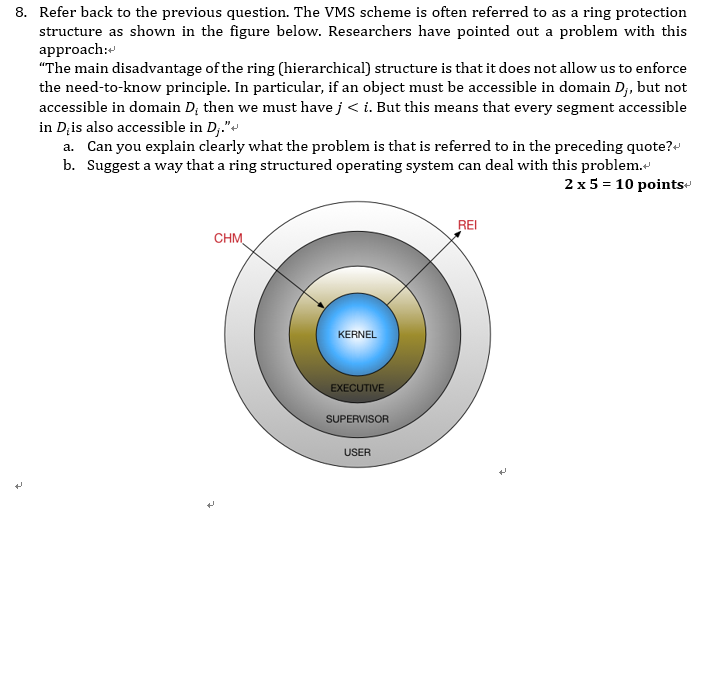
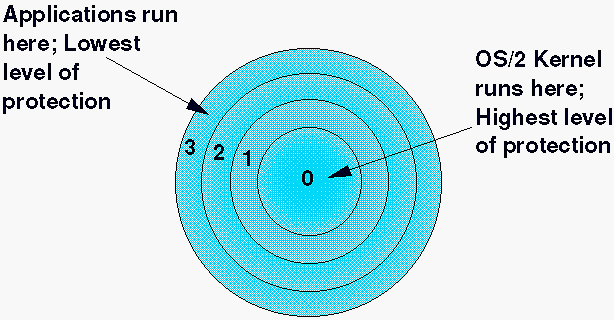
Security Architecture | CISSP Exam Cram: Security Architecture and Models | Pearson IT Certification
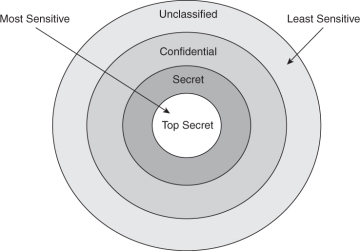
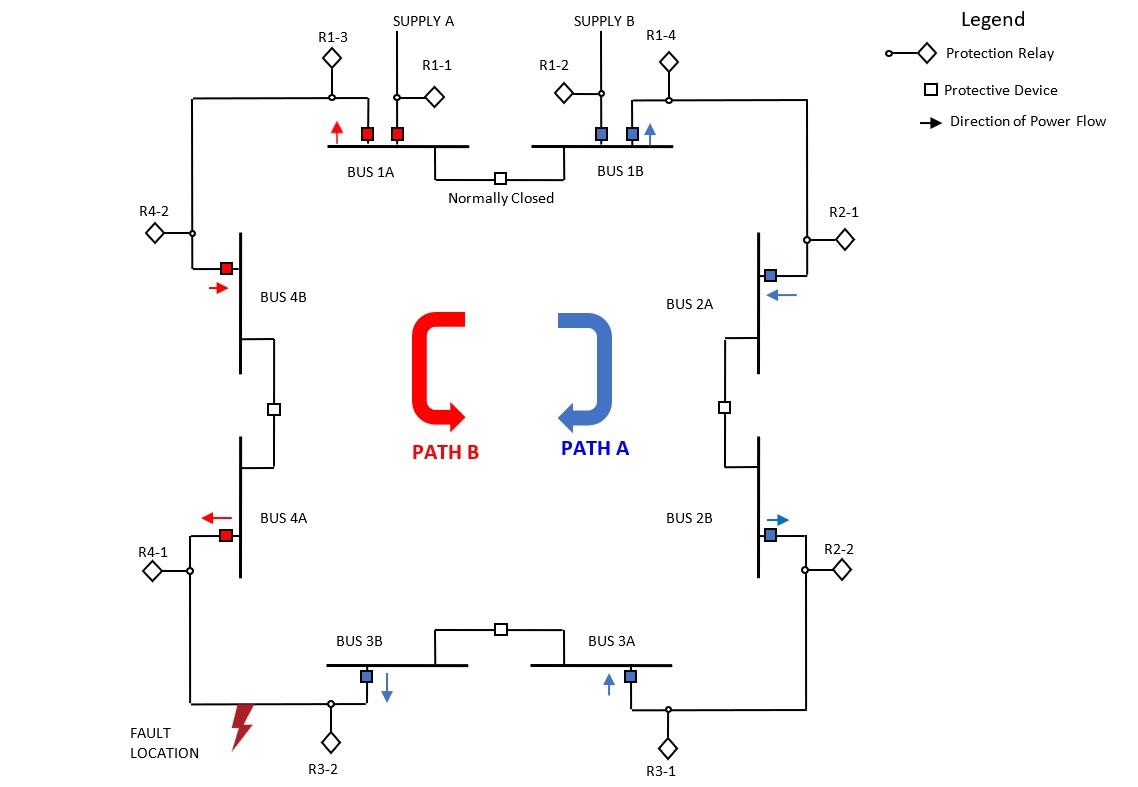
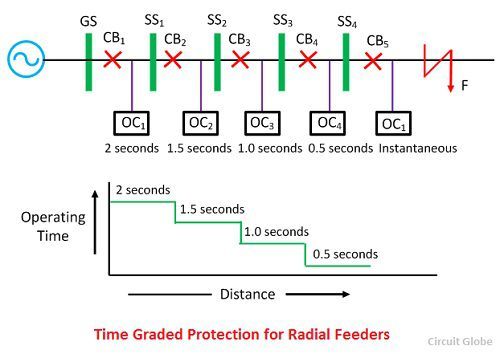
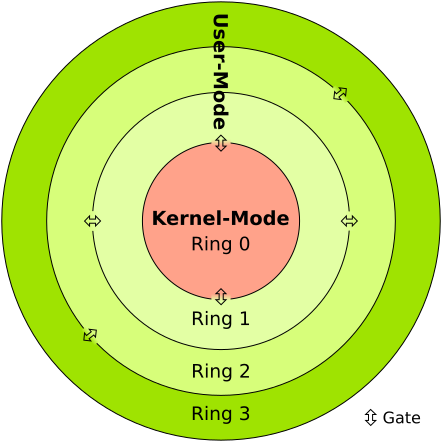
Security Architecture | CISSP Exam Cram: Security Architecture and Models | Pearson IT Certification